This will be a very brief section on VMware security I am not going to cover every aspect of security within VMware but will lightly touch on the commonly used area's. Both the ESXi standalone server and vCenter security is the same, the only difference is where the users and groups come from, if using a ESXi stand-alone configuration they are held locally on the ESXi server, however if you use vCenter you can take advantage of Active Directory (AD) in Windows plus it can be stored locally. Note that users and groups come from the underlying O/S, if using stand-alone ESXi server then the users/groups will be held locally on the server (/etc/passwd and /etc/group), if using a vCenter running on Windows 2008, then these will be local windows accounts or if part of a domain then these will be domain accounts, you cannot administer user accounts or group via VMware only roles.
The VMware model of security involes three components: roles, groups and users, this type of setup is very similar to databases. First you create roles of responsibility then you can add users/groups to allow them to perform tasks. As vCenter has an organization of system folders, datacenter objects and subfolders, a system of inheritance does exist, if you set a role on a folder, it will pass your privileges down the folder hierarchy, vCenter does a good job of hiding objects that a user has no privilege to see. There are 11 predefined roles, I have highlighted which are available to vSphere client and to vCenter
| Role |
Availability |
Description |
| No Access |
ESXi and vCenter |
this role has no priviliges and can be used to deny access to an object. You can use the No Access role to deny a user access to an object when that user has been granted permissions to a parent object. |
| Read-Only |
gives you the ability to only view objects, thus no changes can be made |
| Administrator |
This has the highest level of privileges and thus you can access all objects which includes managing them |
| Virtual Machine User |
vCenter only |
This role assigns a privilege only to VM's, you can power on/off/reset a VM, open a remote console, |
| Virtual Machine Power User |
This extends the role above to include edit some of the VM settings, create and revert snapshots |
| Resource Pool Administrator |
This role has the ability to create resource pool of CPU and RAM and allocate groups of VMs to the pool |
| Datacenter Administrator |
This role allows you to create datacenter objects but you have very limited access with VM's. |
| Virtual Machine Administrator |
This role allows full control over VM's inclduing deleting them. |
| VMware Consolidated Backup User |
Allows just enough privileges for Consolidated backups to function |
| Datastore Consumer |
It has only one privilege the ability to allocate space to a datastore |
| Network Consumer |
it has only one privilege "assign network to a virtual machine, host service console, VMKernel virtual NIC or physical" under the network privilege |
Roles
So lets create a role and assign some privileges
| Roles |
To create a role, from the home page in vCenter select "roles" from the administration section
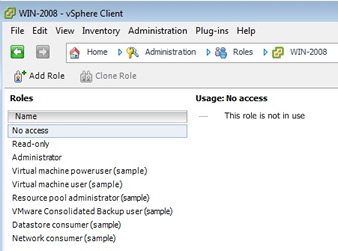
select "add role", and type in a meaningful name, then start selecting the privileges for this role, I am not going to cover all the privileges here, I have just selected "virtual machine", this in itself greatly expands into many privileges.
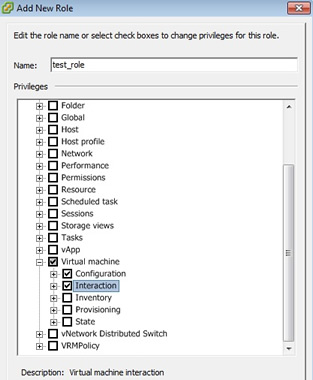
As you can see the new role appears at the bottom
To remove a role just right-click that role and select remove, you also have the ability to clone roles and then change them a little
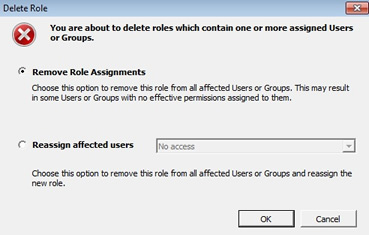
One note about removing roles you may see the below warning message, this is justing letting you know what you want to do about the existing users within this role, either leave them with no access or assign them to another role.
|
Using Roles and privileges to access a certain VM can a bit of a task as you need to create the privileges from the top down, first start with the datacenter folder, then down to the ESXi hosts and finally the VM itself
| assign a privilege |
First select the area that you want to add a privilege to, this could be a folder, host or a VM, in the example below I have selected the production folder, the panel on the left is what appears first, you can change the assigned role to your newly created role, then you need to add users or groups, this is done by selecting the "add" button which produces the right-panel. here you can choose from your user/group list, remember these will either be local accounts or domain accounts depending what you have setup
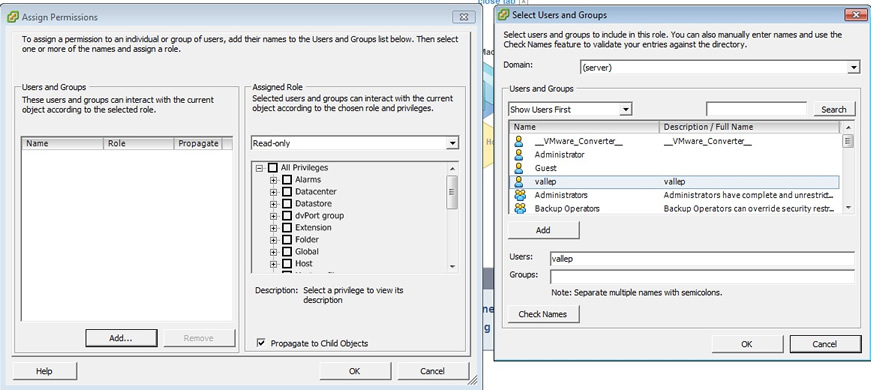
When you have choosen your users/group you should see something like below, here I have allowed a user called vallep to have read-only access, thus when I login via vSphere client or vCenter using the vallep account I will only have read-only access and will not be able to change anything.
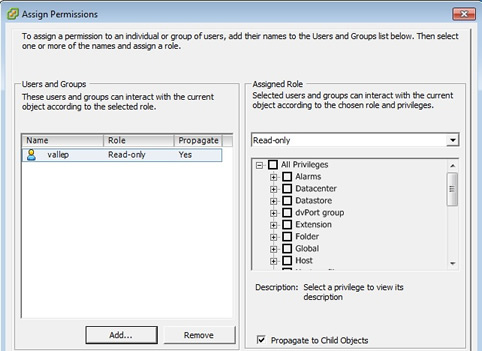
Once you have added some users or groups you can go back to the role home page and see the changes you have made, you can clearly see the hierarchy format used.
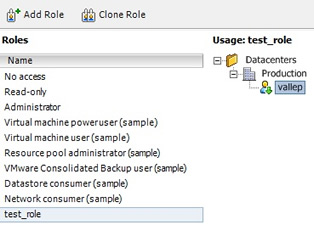
|
Personally I just stick to the already created roles and generally do not need to create additional roles, most of the time I can get away with using the administrator, virtual machine user and read-only roles. Lastly I just what to touch on the ESXi default accounts that are created there are 4 of them,
| root |
this account has full access, by default the password is blank when you have just installed ESXi, it is also used when you add you ESXi host to vCenter |
| dcui |
this account primary role is to configure hosts for lockdown mode from the direct console, the user is used as the agent for the DCUI and should not be modified or used to login to your ESXi server |
| nfsnobody |
this account is used to access NFS datastores |
| vpxuser |
this account is used by vCenter to issue commands to your ESXi server regardless of the end user that is connected to vCenter server, this user is granted the administrator role. |
Datastore Access
If you want to improve on security regarding the datastores within vCenter, you should create folders and then drag and drop the datastore into the folder, after which you can assign permissions on that folder restricting the access to the datastore, here is what I have done with my test environment, I created four folders and placed the datastores into the folders, I could then place different permissions on each of the folders.
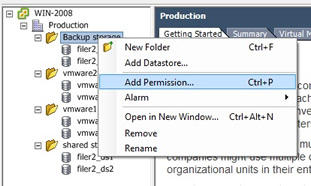
I will come back to this section at a later date to update it with advanced security features but thats all i am going to cover for now.







