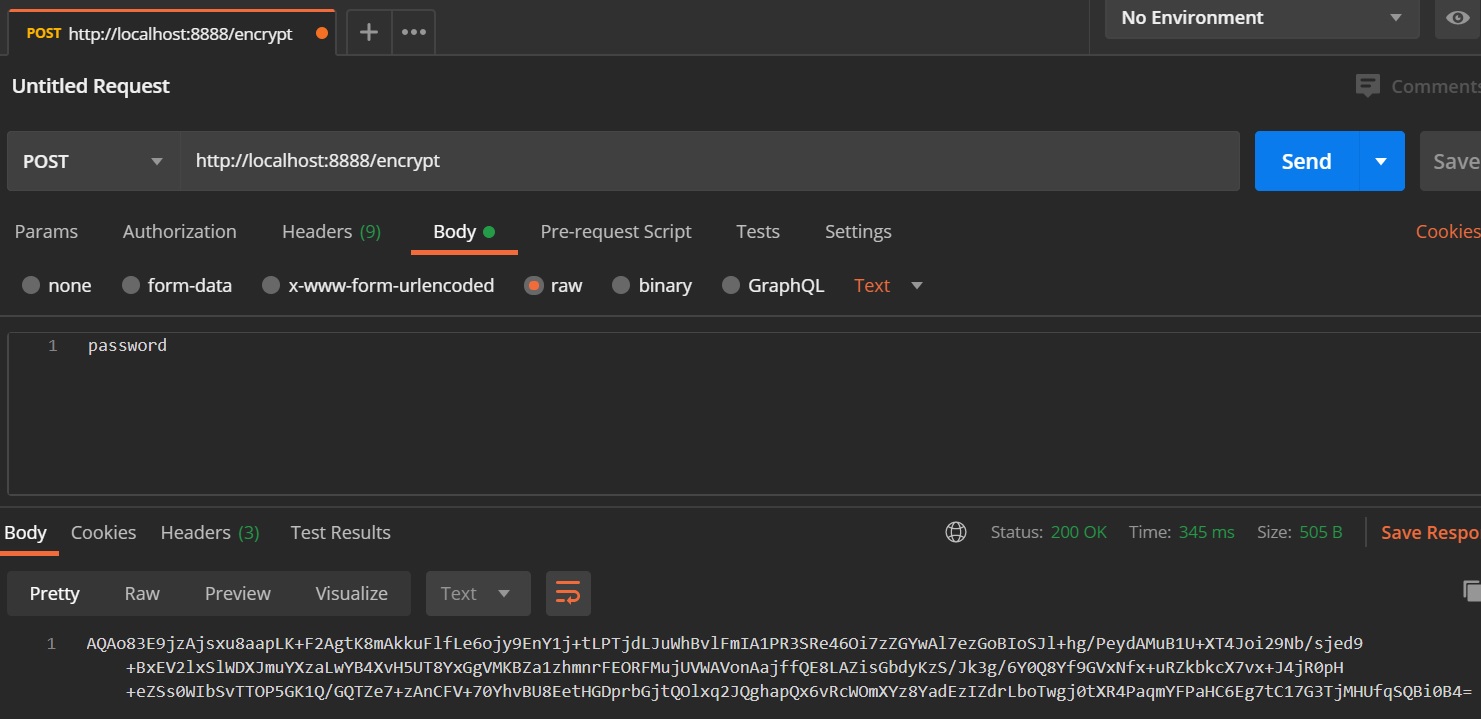
When creating a Spring Cloud application you might have noticed that configuration (application properties) is littered all over the place and this means more headache when changing the configuration for some services, it would be ideal if we could have just once place that is centralized to handle all the configuration (for example one place for the database details), enter the Spring Cloud Config Server, as you can see in the diagram below the Spring Cloud Config Server will handle all the property files for the application in one location, but as a added bonus we can also get the application to re-read the config server propery file if it has changed, I will explain this later (Spring Cloud Bus using RabbitMQ). The property files can also be held in a GIT repository that the Config Server will have access to, also we can use secure file storage and even a secure vault, pretty cool. You can also still maintain a local properties file but the config server will have a higher priority and thus you should keep the global configuration in the config server for example the database details.
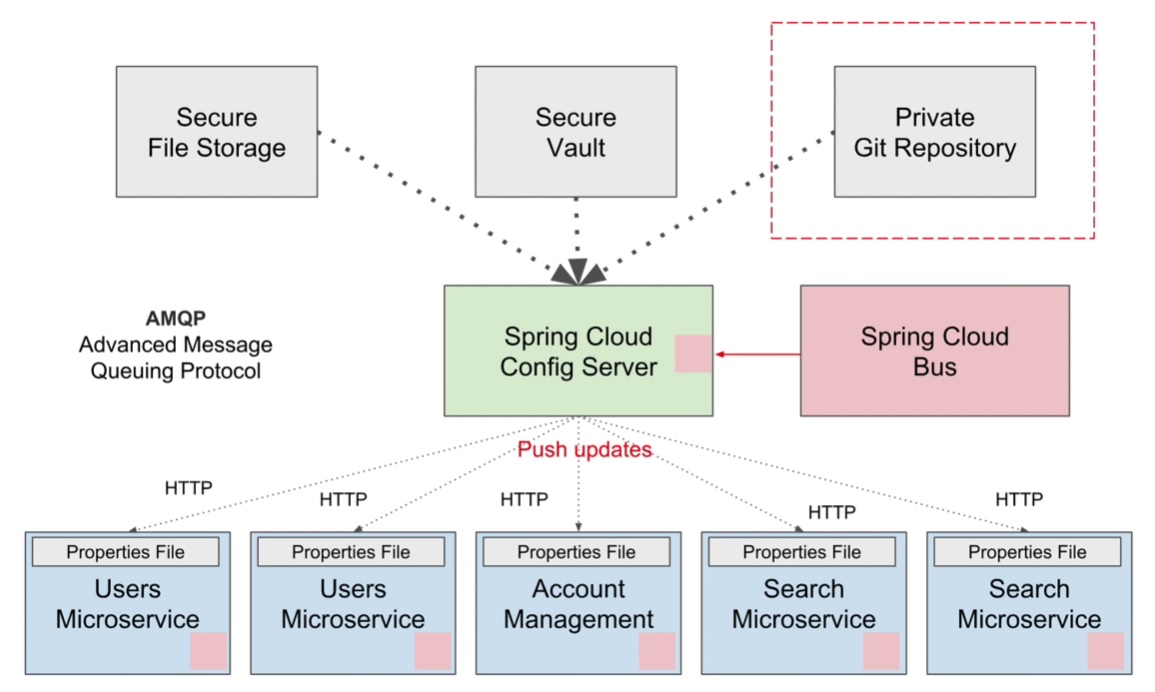
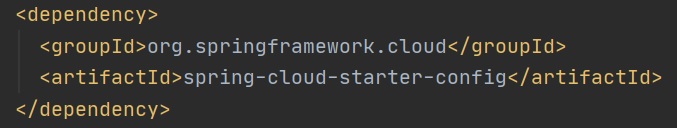
The Spring Cloud Config Server is a spring application, pulling in one dependency as per below
We then add some properties to give the application a name and define the port which the config server will run on (left-hand screenshot), We then enable the config server using the @EnableConfigServer annotation (right-hand screenshot).
 |
 |
There is nothing special about the config server property files, you can also use profiles and properties file which I covered in my Spring Boot tutorial as per the diagram below, the only thing to bear in mind is the priority which the config server has the highest.

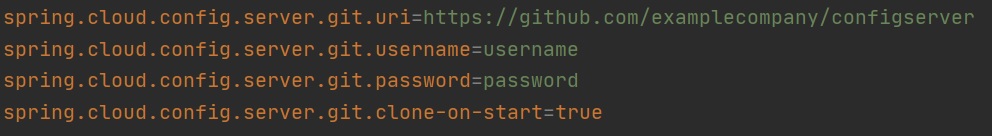
To configure the config server to access a GIT repository, we have to add some properties to the properties file as per below, the config server will also use SSH keys (if setup) out of the box instead of username and password.
You can then create the property files in the GIT repo, remember there is nothing special about them, they are just ordinary property files.
 |
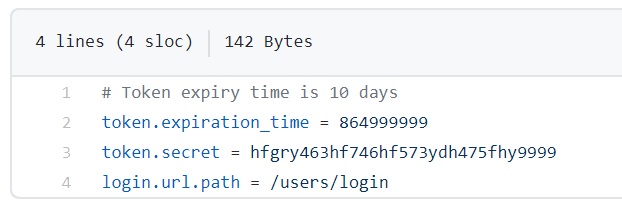 |
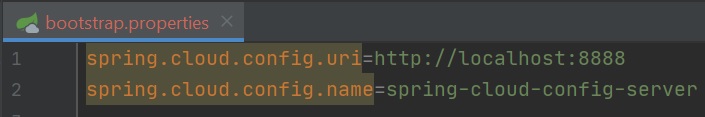
Now we have setup the config server how does the microservice application use the config server, first we pulling in a dependency (left-hand screenshot) and then add a bootstrap.properties file which will be called before the application.properties file, in this file we add two properties to point to the config server (they should match whats in the application.properties file of the config server). Thats it the microservice appliation will now also use the config server (which uses GIT) for property files as well. Also you can even point the Zuul API Gateway application to use the config server.
 |
 |
The next step is to config the Spring Cloud Bus which I have a separate section.
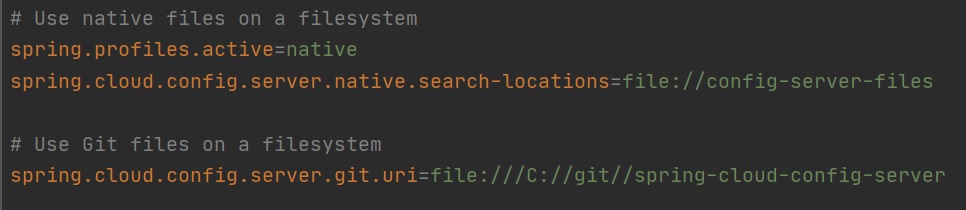
Lastly you can also setup to access a local filesystem using either native files of files that are in a GIT repo, the properties to do this are below
You can also see what files and properties are configure by sending a GET request to the config server, you can either send directly to the config server or via Zuul API Gateway which will route to the config server, the ouptut is in JSON format.

Encrypting and Decrypting Property Files
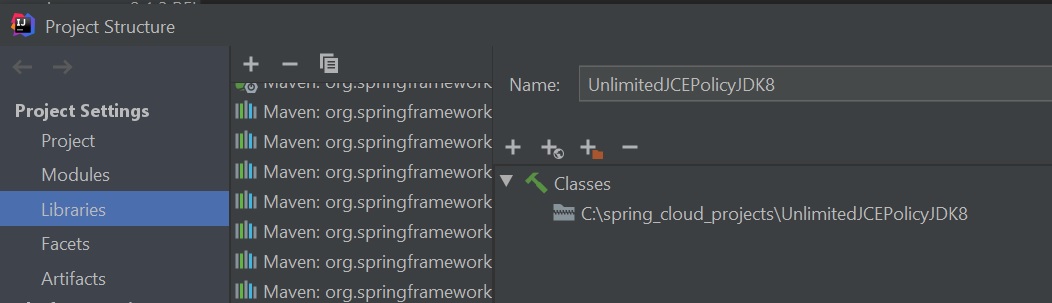
In this section I will show you how to encrypt and decrypt your property files for added security, If you are using an older version of Java you need to download the Java Cryptography Extension (JCE) from Oracle, I expanded it in to a directory (left-hand screenshot), I then made Intellij aware of this jar directory (right-hand screenshot), these files also need to be copied into jre/lib/security folder for example my jdk 8 version would be C:\jdk1.8.0_161\jre\lib\security. I am using JDK 11 so this already comes with these.
 |
 |
We will start looking at symmetric configuration first, we need to create an encryption key however this must load up before any property files and to do this we create a bootstrap.properties file as per below
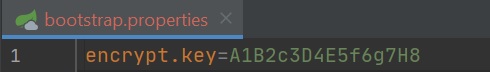
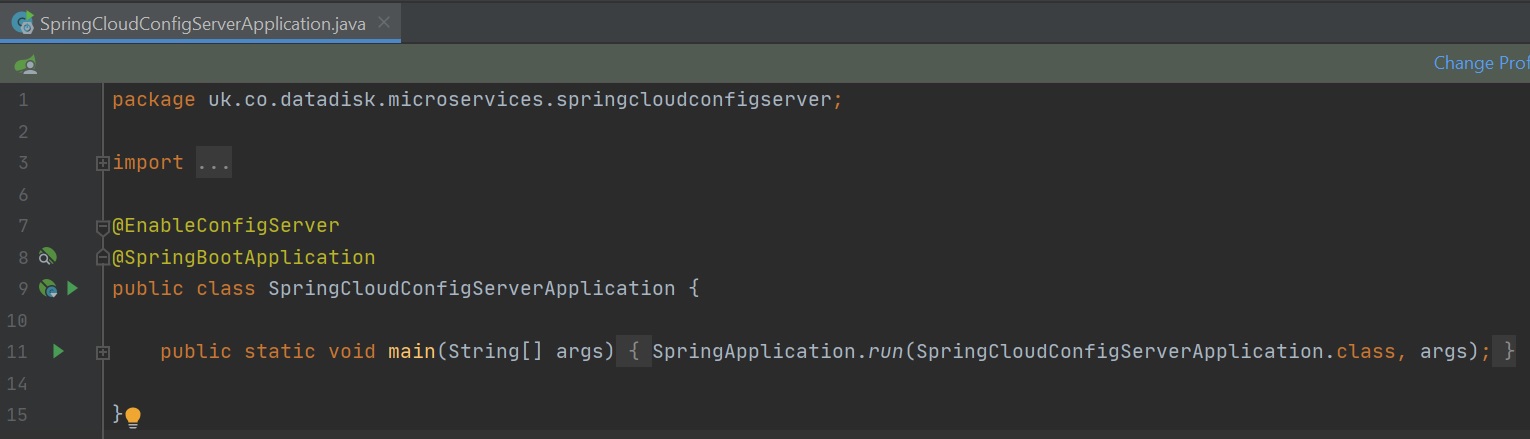
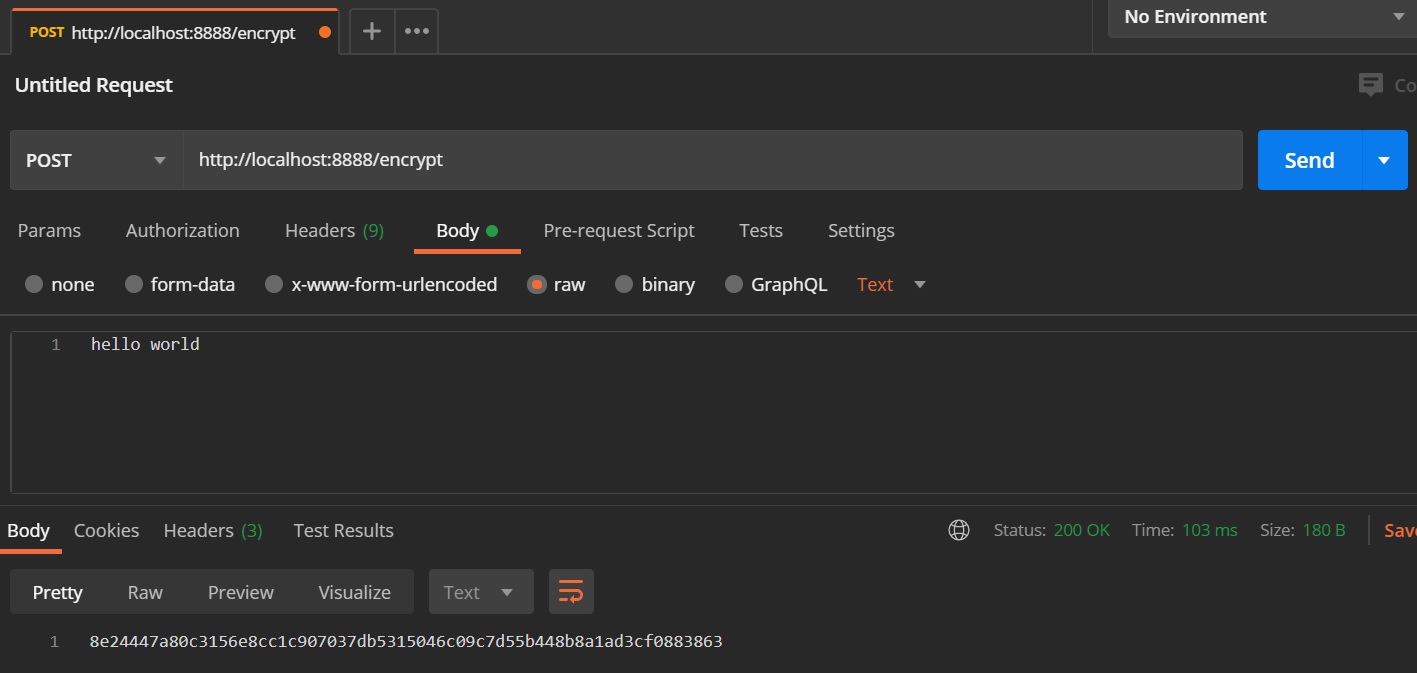
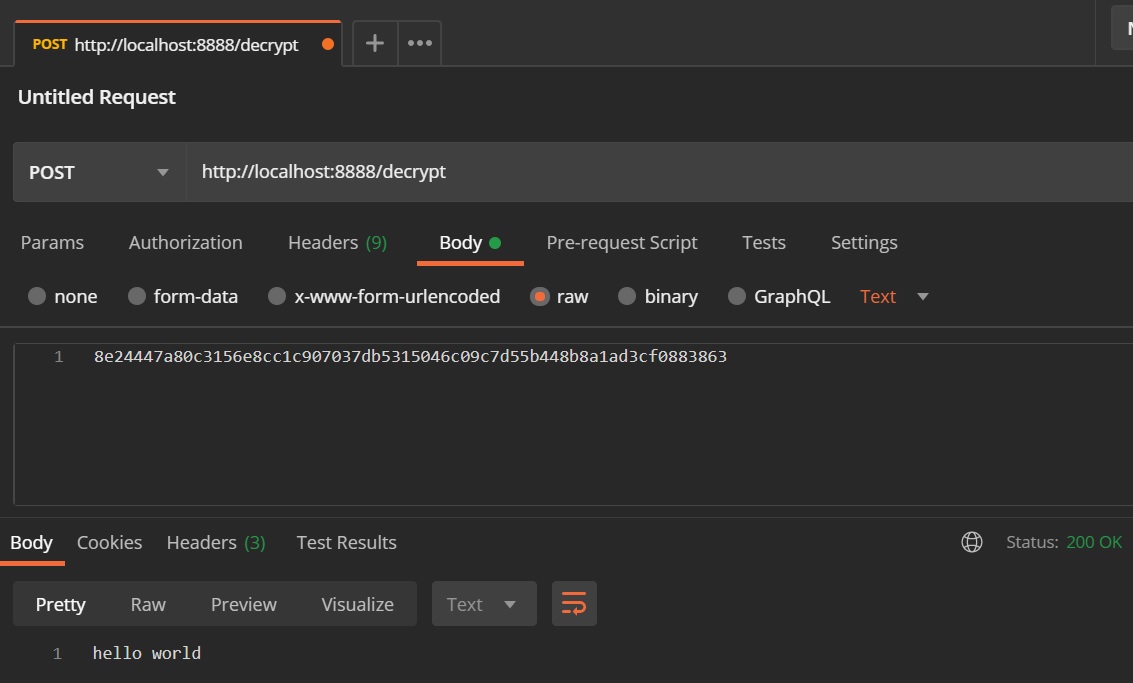
Restarting the config server we can now test to see if encryption works using Postman, I create a POST request to the URI /encrypt and in the body I put plain text that I want encrypted, the response back is the plain text encrypted, I can then take that encrypted text and decrypt it using Postman again but using the URI /decrypt, can can bee seen below. You can use the below to encrypt plain text that can be used in a property file.
| Encrypt Test | Decrypt Test |
|---|---|
 |
 |
We can now encrypt plain text and use it in a property file as per below, notice the curly braces and the word cipher, there is no space between this and the encrypted text. Use this to protect passwords, token secrets, etc.
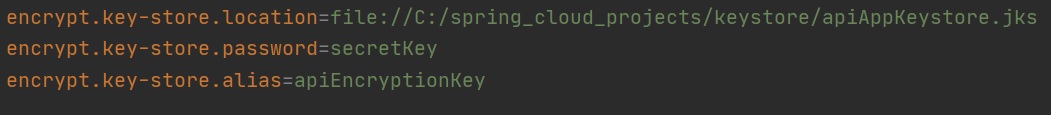
You can also create a asymmetric keystore which is more secure, first you need to create the keystore using the below, feel free to change anything to reflect you environment
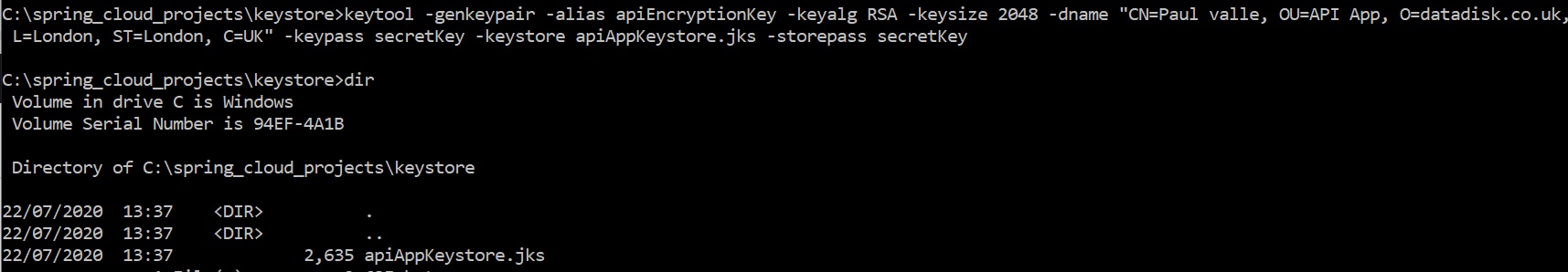
Then we add the below properties to the proerty file
Then its the same as above for testing and encrypting properties in the property file, you will notice that the encrypted text is now longer and thus harder to crack.